development
Fixing a WordPress redirect attack

This blog will detail how to fix a WordPress redirect attack. Although I'm not an expert on WordPress or malware attacks these are the steps I took to help a charity organisation recover their WordPress site. The organisation which will remain unnamed for privacy reasons had no website backup and had already been charged over £200 for a previous backup that was also infected with malware by their hosting provider.
At a loss, a friend within the organisation approached me asking if there was anything I could do to help recover the site. Otherwise, they would be forced to possibly pay another fee for a backup or a further fee to have the malware removed from the site. I figured I could try my best to help, with it being a non-profit organisation very close to my heart.
Here are the steps I took to recover the malware-infected website without a backup, this required a substantial amount of manual clean-up so if you can restore from a backup I would advise to try that first.
Step 1:
Try navigating to the site admin access portal the URL may look something like the following:
HTTP://<Your site URL>/wp-admin
If you're getting redirected to a malicious site when hitting this URL continue with the steps!
Step 2:
We've sussed that it's definitely a redirect attack - now what we need to do next is access your WordPress files on the server that's hosting your website. If you go to your hosting provider they may have steps you can follow to use FTP to access the files directly on your server.
Once you've connected to the server and are able to move and remove files directly from the server, navigate to the WordPress plugin files. Begin to one by one go through and re-download the source file for each plugin, that are used on the site from the WordPress plugin site.
It might be an idea before doing anything directly to the site itself to make a backup of the infected site. This will just ensure if you need to look back on anything, you can, before we go any further. Next what we'll do is replace each of the plugins, if you rename the already existing files by appending 'old' to the front of each plugin name. Then add the new downloaded plugins. What we are doing is just replacing all plugins that may be infected with malware with fresh downloads, which we can assume shouldn't contain anything malicious.
Step 3:
You'll want to do something similar for the themes within your website too, re-download any WordPress themes you have and replacing the existing themes in the themes directory with the new versions.
Step 4:
Once you have replaced the plugins and themes have a browse through the following files - or anything that may look suspicious.
- index.php
- index.html
- .htaccess
In the case of the website, I found a folder called 'Fraudo' that contained malicious code, which was getting generated every-time the website URL was hit. I searched to find the code that was re-adding this folder to the directory each time even after it was deleted you may need to do the same if you are seeing something similar.
Important to note I also found malicious code hidden in image file types. I realised that some images had been copied and renamed slightly, look out for this. Once I converted these to txt files I could see they contained malicious code and removed them from the site.
Step 5:
You'll want to check the WordPress database. This is where all the necessary website data about the site is stored, including the site URL and bingo, this is where I needed to clean out a lot of the malicious site URLs. Take a backup of the database before executing any SQL statements, just so you can refer back to it if needed.
If you're wondering how you access your WordPress database you'll actually find the plain text username and login password in one of the php files in your WordPress site. I learned that this is how WordPress actually gains access to the database, by just reading it right out of the file (As a non-WordPress developer I thought this was a massive security flaw - but moving on).
First, have a look at the wp-options table (this may be renamed on your side but will usually be appended with 'wp-' then options something) and look for a suspicious link it may end in '.ga'. Once you have found a suspected suspicious link you can run the following SQL statement in each table to ensure that any malicious links are removed from the WordPress site.
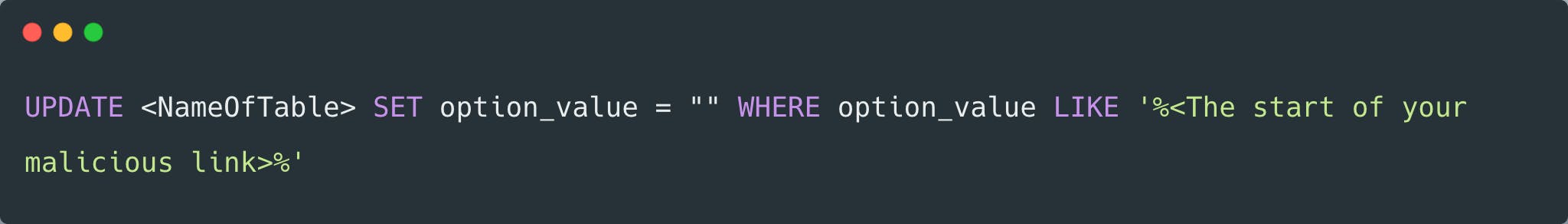
I would recommend if you can have a look through each table in the WordPress database to ensure you've removed all the appropriate suspicious links/entries.
Step 6:
Ensure the site_url row in the database wp_options table now points to the correct domain instead of the malicious site, you can do this by directly editing the URL entry.
Once you've updated the database, and with the site_url now pointing to the correct domain you can access your WordPress admin portal!
Once you have accessed the portal delete any suspicious user accounts that may have been added. WordPress hackers tend to add an admin level user so they can log in later and do the same thing again after you've fixed the site. Also, change the admin level password and all passwords of other users on the site. I wouldn't recommend using the WordPress auto-generated password instead opt for your own unique secure password.
Step 7:
Take a backup of both the site and database and do this on a regular basis with different versions! I recommend if you aren't already, storing your WordPress source code on GitHub or GitLab in a private repo.
Finally, follow the steps in this article to secure your WordPress site, it has some great tips in making sure something like this doesn't happen again.